– Basic version | Switch to Advanced Version
A basic introduction to the AZTEC Ceremony, and why we need to run it.
{{blog_divider}}
The UTXO
AZTEC’s core transaction is a confidential UTXO — just like Bitcoin.
An Alice-and-Bob explainer as follows:
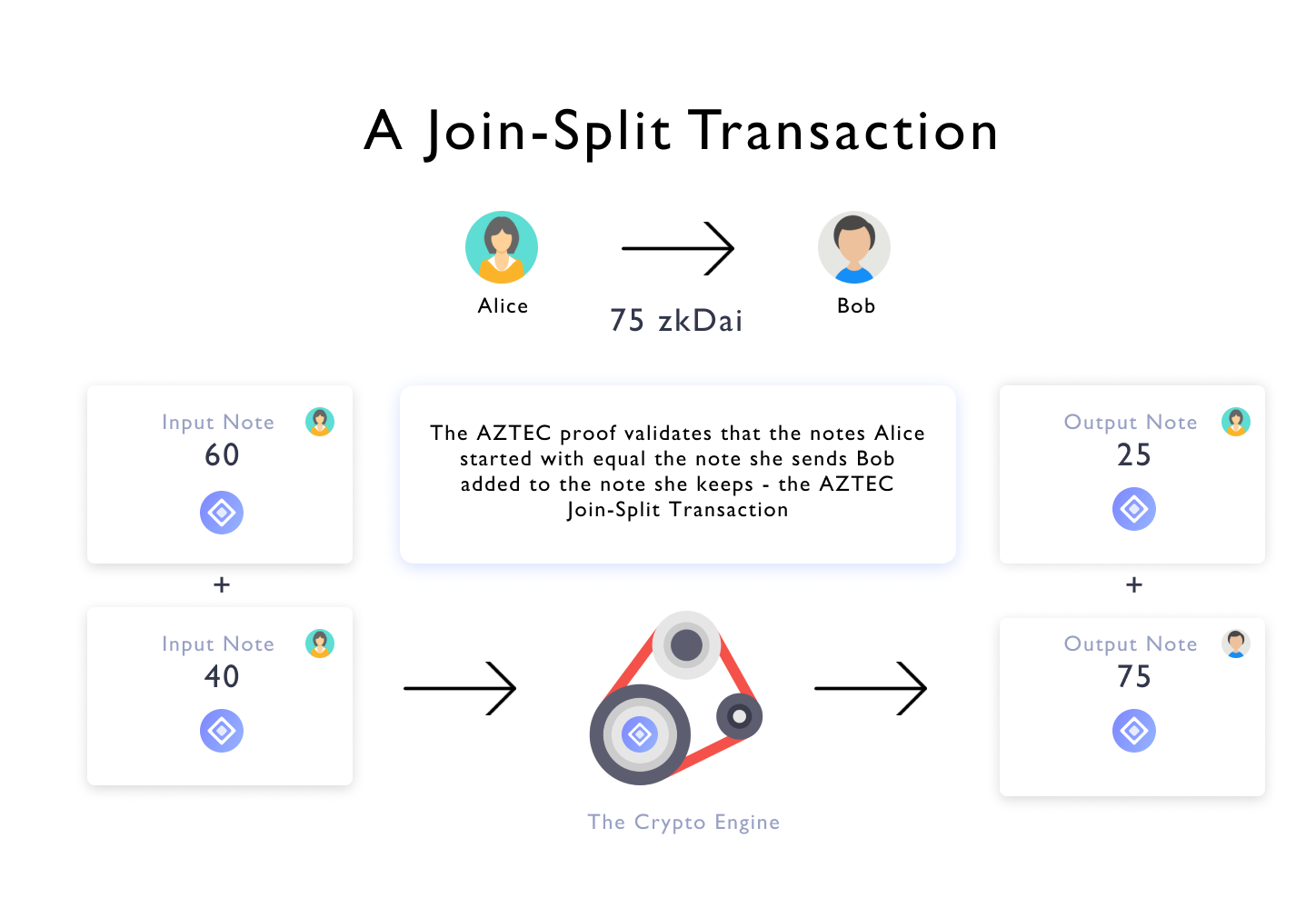
Suppose Alice has a cluster of notes summing to 100zkDAI, and wants to send 75 zkDAI to Bob— we’ll handle this much like change in a shop.
Alice takes notes of size 60 zkDAI and 40 zkDAI (these are now called input notes — she needs both, because neither can cover the 75 zkDAI she’s wiring to Bob), and she will create two output notes — 75 zkDAI for you, 25 zkDAI for me.
Note this is exactly how Bitcoin works — but AZTEC transactions need to be confidential. And Ethereum needs to validate them — i.e. check that 60 + 40 = 75 + 25.
But just how do you check this on encrypted numbers?
{{blog_divider}}
Elliptic Curve Numbers
AZTEC maps each integer onto an alien number system that rules the roost in blockchain technology today— an ‘elliptic curve over a finite field’.
Elliptic curves preserve addition —what does that mean? Well, it lets Ethereum check that the encrypted $100 you started with (before your transaction) is equal to the sum of the following:
- The encrypted $75 you’ve sent
- The encrypted $25 you’ve kept
— and Ethereum can verify this without knowing what numbers are buried inside.
{{blog_divider}}
The Snag with Encrypted Numbers
These number systems are a bit odd — they work like an enormous clock —when you get to a huge number (of the order 2²⁵⁶) — you actually go straight back to 0 again.
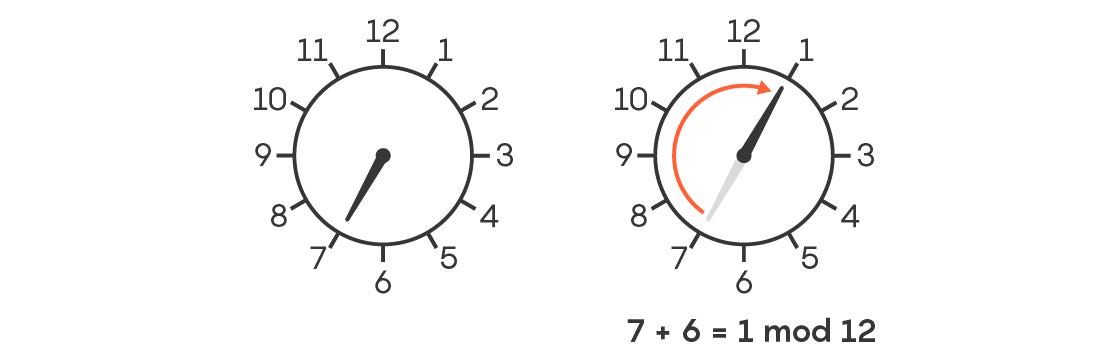
And that’s a problem.
Why? Because if, each transaction, Ethereum only checks that the notes spent are equal to the notes created, then you can easily attack it. After all, -1 (being the number just before 0) is equal to an enormous positive number (again, of the order 2²⁵⁶) — we’ll call this number BigNum.
So you can produce output notes of size $101 and $(BigNum-1) — and those, in this strange new world, sum to $100.
So what’s the solution?
A Range Proof
Here’s the solution — force every user of the system to prove that their output notes are quite small compared with 2²⁵⁶. If you can, they can’t make their notes big enough to wrap around, and that will satisfy Ethereum that no one’s cheated.
{{blog_divider}}
AZTEC’s Range Proof
The AZTEC Range proof puts a premium on efficiency.
We provide a Codex of points signed via so-called Boneh-Boyen signatures. This Codex consists of the signed numbers 1, 2, … Max.
We then stipulate that, for a transaction to be approved by the AZTEC Cryptography Engine (ACE), the user must prove they formed the output notes from the Codex — otherwise the proof fails.
{{blog_divider}}
Building the Codex
This is the purpose of the trusted setup. In two phases it builds up the Codex of points:
- The Relay — building a large number of points with mathematical relationships to one another (called monomial points), by passing around a transcript. Each participant needs to roll their own random number into the transcript (which cannot then be extracted from the new transcript). They must then destroy that number
- Post Processing — constructing the Codex from the building blocks created in the relay phase
It is Phase 1 that is critical to the Ceremony’s security. However, it would require every single participant behaves dishonestly. If just one participant follows the rules, the setup is secure.
So now you know what’s going on under the hood.